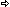- Performing Post-Installation Operations
- Configuring Advanced Settings
- Configuring Alerts
- Configuring the Discovery Overrides
- Configuring Logs
- Filtering Elements to Monitor
- Configuring the Sessions Monitoring
- Configuring the Specification Backup Restriction Window
- Configuring the Mount Requests Monitoring
- Configuring the Mount Requests Date/Time Format
- Configuring the Multi-Node Monitoring Mode
- Configuring the Node Status
-
Home
- PATROL
Configure HP Data Protector KM
This section explains the settings required to configure HP Data Protector KM via a PATROL console.
Performing Post-Installation Operations
It is recommended to perform post installation checks once the KM is installed and loaded on the PATROL Console to ensure it properly operates. Post-installation operations include:
- Configuring Data Protector Nodes Monitoring
- Configuring the KM user account
- Verifying:
- Restarting the PATROL Agent and PATROL Console.
Configuring Data Protector Nodes Monitoring
HP Data Protector KM allows you to monitor several Data Protector cell managers with one PATROL Agent. The configuration procedure is as follows:
-
Right-click the HP Data Protector main instance > Configuration > Data Protector Nodes…
-
Specify the Data Protector server details:
- Node ID: Enter an ID for the Data Protector node. This information is only required if a unique ID cannot be generated using the hostname provided.
- (Required) Hostname/IP Address/FQDN: Enter the hostname, IP address, or FQDN of the node to be monitored.
- (Required) System Type: Specify whether the Data Protector node is a UNIX/Linux or Windows system.
- (Required) Status: Select Enable to start the Data Protector node monitoring; Disable to stop it.
-
Check the Create a separate device in TrueSight box if you want the Data Protector nodes to appear as a separate device in TrueSight OM.
-
Click Update.
A Data Protector Setup node instance (Data Protector Setup: <node-id>) appears in the PATROL Console but the monitoring will not start until the appropriate credentials are entered using the Configuration > Login KM Command.
Configuring the KM User Account
A user account with administrative privileges must be configured in BMC PATROL or BMC TrueSight Operations Management to read and execute HP Data Protector application programs and access file systems. Depending on the operating systems used, several options will be available. For more information, refer to Security Requirements.
To configure the KM user account:
-
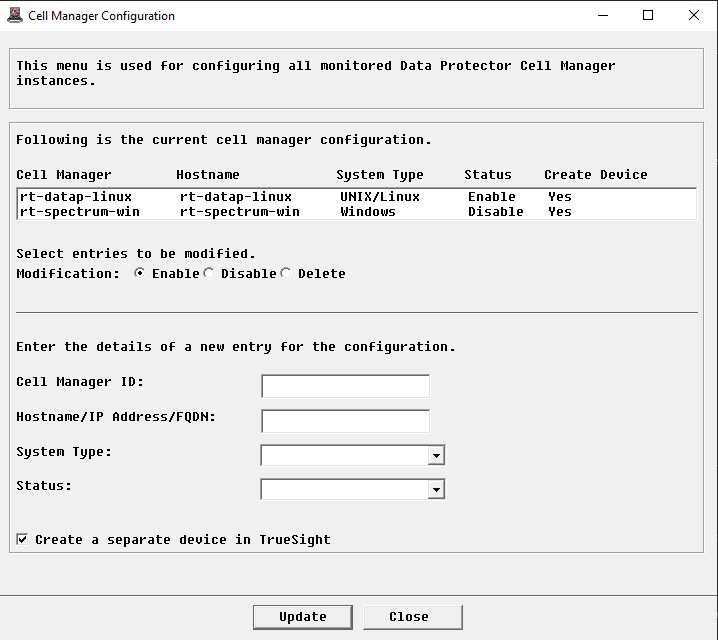
In the Console, right-click the host instance > KM Commands > Configuration > Login… The Login Configuration dialog box is displayed:
-
To use:
- the default PATROL Agent Account, check the Use Agent Default Account box and leave the Username and Password fields empty
- a different user account, enter the login details in the Username and Password fields
-
If a sudo user account is used:
- check the Use Sudo box
- click SUDO Binary File to verify the sudo binary file path
-
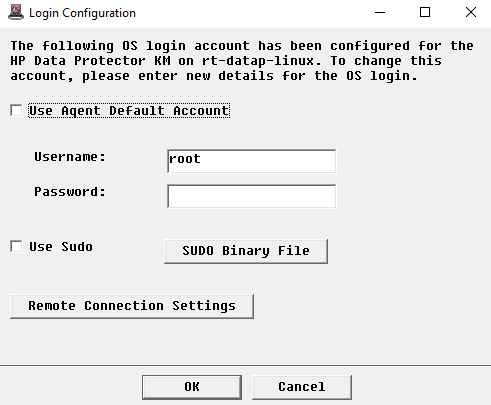
If you are monitoring a remote host, click Remote Connection Settings:
- Connection Timeout (in Seconds): Enter the number of seconds after which the connection to the remote node will timeout.
- Maximum Connections: Enter the maximum number of simultaneous connections allowed to the remote node.
- Click Accept.
-
Click OK.
If the credentials are not valid, the HPOLoginStatus parameter will appear in “suspicious state” after the next data collection.
Verifying the Application Discovery
To verify the application discovery:
-
Check that the Data Protector Setup instance changes to display the server type. If not, check the message in the Data Protector Setup instance and in the PATROL Console System Output Window (SOW) or in the log file <PATROL_HOME>/log/HPO_<port>.log. You can force a full discovery by right-clicking the Data Protector Setup instance > KM Commands > Force Discovery.
-
Check that the application class instances are actually instantiated. The initial data collection may take some time depending on the complexity of your environment (up to one hour). If needed, force a data collection by right-clicking the server instance > KM Commands > Refresh Parameters.
If the Data Protector server is configured in a clustered environment, you will have to enable multi-node mode monitoring.
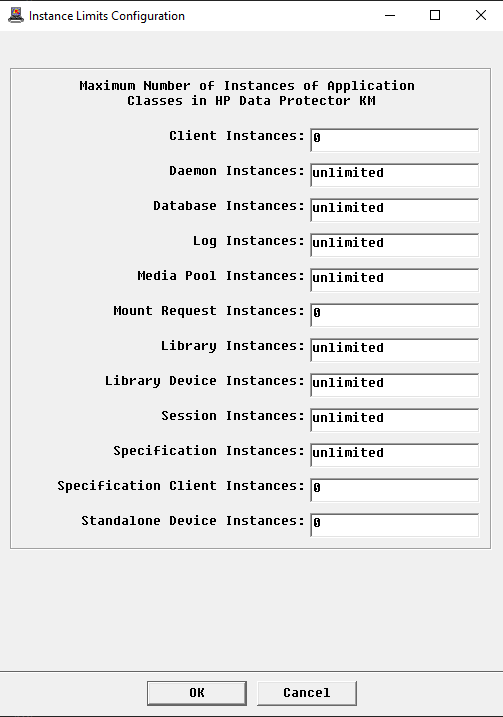
Configuring the Instance Limits
HP Data Protector KM monitors all the elements discovered, except for Clients, Specification Clients, Mount Requests and Standalone Devices that are disabled by default. This may represent an important workload to the PATROL Agents and console. Because the monitoring of some elements may be irrelevant for various reasons, you can apply filters to indicate which elements will be monitored or not.
To modify the default configuration:
-
In the Console, right-click the server instance > KM Commands > Configuration > Instance Limits…
-
Enter the number of instances to be displayed in the console for each monitored element
-
To disable the monitoring of a specific application class, enter 0 (zero) in the relevant field
-
Click OK.
Verifying the Initial Setup
To check the initial setup of the KM:
-
Check for any error on the PATROL Console System Output Window (SOW) or in the
<PATROL_HOME>/log/HPO_<port>.log. -
Check whether the discovered files and directory paths are correct, using the menu Configuration > Paths… from the server instance.
-
Refer to the label of the server instance to check whether the discovered node type is correct. The node type can be modified, using the menu Configuration > Node Type… from the server instance.
-
Check the Infoboxes and Parameters of all the HP Data Protector KM instances and verify that they are properly set.
-
Under each container instance, open all detail parameters (text parameters with names in the format
HPO<Object>Details), and check for error messages. -
Check the new value of the HPOLoginStatus and HPONodeStatus parameters set after the completion of all data collection. If either is not in OK state, open the annotation point to determine the cause of the error. HP Data Protector KM will check the status of the node using command
omnisv -status. Any errors in the result will set the parameter HPONodeStatus to trigger a warning or alarm. This error filter can be changed through the menu Configuration > Node Status…. Refer to Configuring the Node Status for more details. If the query cannot be executed, the KM will check the existence of the following daemons to determine the status of the node. By default, these daemons are sought:On a UNIX/Linux Server:
Daemon Description crs Cell Request Server mmd Media Managerment Daemon On a Windows Server:
Daemon Description crs.exe Cell Request Server mmd.exe Media Managerment Daemon OmniInet.exe OmniBack II Inet Service -
After the KM has been running for at least an hour:
- Right-click the server instance > KM commands > KM Status… from the HP Data Protector instance. A report is displayed, detailing information on the managed system. Check through the report for any warning or alarm. If any error is found during any of the above steps (including any incorrect data in Infoboxes or any warning or alarm in the KM Status report), determine the cause(s) and take steps to resolve these errors. You may need to refer to the User Guide, or contact Technical Support, attaching the KM Status report.
- If needed, click Save As Task to open the report in a task window. You could later save it as a text file or print it.
Restarting PATROL Agent and PATROL Console
Restarting the PATROL Agent and PATROL Console is optional but often a good practice to confirm that the HP Data Protector KM operates correctly.
In addition, the PATROL Agent restart will force all KM discoveries and data collections to start immediately.
Configuring Advanced Settings
Configuring Alerts
Configuring Alerts Rules
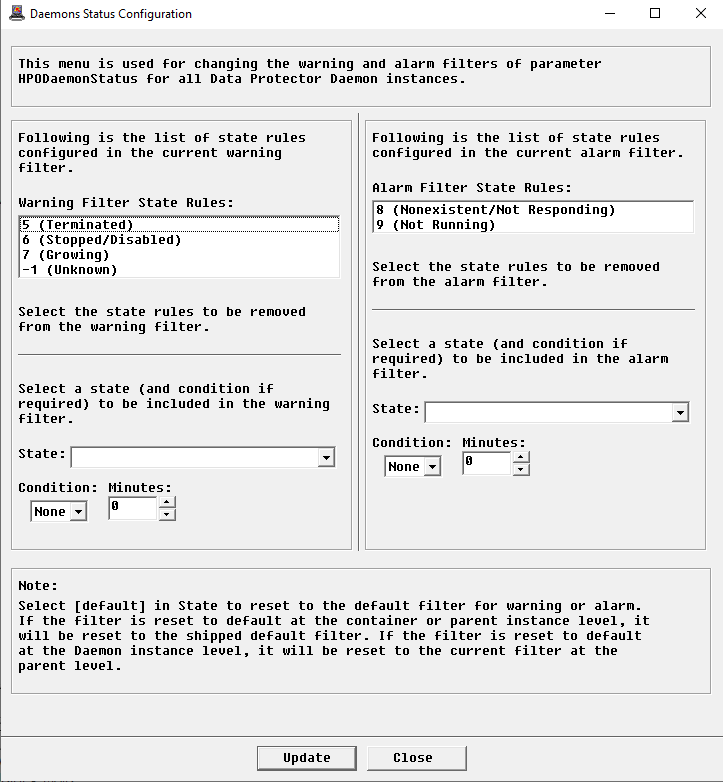
The status of an element is determined by the State parameter and by the status mapping rule. This mapping rule indicates which states will trigger a warning or an alarm on the Status parameter. It can be configured as follows:
-
In the Console, right-click one of the instance for which you want to configure the status and select > KM commands > Configuration > Instance Status…
-
In the Warning Filter State Rules list, select the states that will not trigger a warning
-
If needed, apply a time condition to a specific state. For example, if you want to trigger a warning when the Growing state of the Daemon instance lasts more than 600 minutes:
- From the State list, select 7 (Growing)
- From the Condition list, select >
- In the Minutes field, enter 600
-
In the Alarm Filter State Rules list, select the states that will not trigger an alarm
-
If needed, apply a time condition to a specific state. For example, if you want to trigger an alarm when the Not Running state of the Daemon instance lasts more than 30 minutes:
- From the State list, select 9 (Not Running)
- From the Condition list, select >
- In the Minutes field, enter 30
-
Click Update. The mapping rule will be applied to that specific instance.
To revert to the default status mapping rule for either filter, select [default] from the list of states and click Update.
-
Resume the procedure for all the instances for which you wish to apply monitoring filters.
Configuring Alert Acknowledgement
By default, alerts will automatically be acknowledged unless you modified the settings to allow manual acknowledgement.
Please note that manual acknowledgement may impact the performance of the application and of the PATROL Agent if the number of alerts waiting to be acknowledged constantly increases.
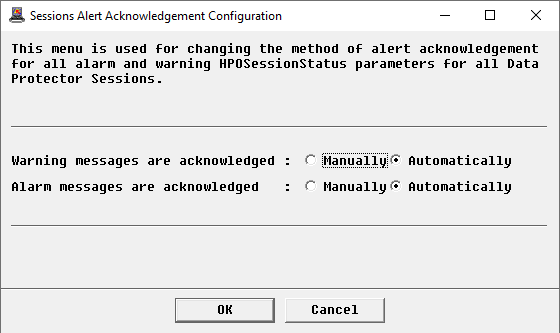
Configuring Sessions Alert Acknowledgement
By default, the alerts triggered on the HPOSessionStatus parameter for the completed sessions are automatically acknowledged in the next collection cycle. If you want these alerts to be manually acknowledged, you will have to configure the session alert acknowledgement as follows:
-
In the Console, right-click the Sessions instance > KM Commands > Configuration > Sessions Alert Acknowledgement…
-
Indicate whether the warning and alarm messages will be manually or automatically acknowledged
-
Click OK.
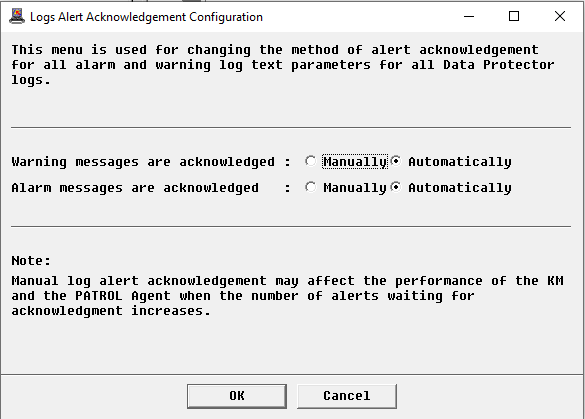
Configuring Logs Alert Acknowledgement
By default, log alerts are automatically acknowledged when new ones are detected. To change the default behavior:
-
In the Console, right-click the Log(s) instance > KM Commands > Configuration > Log(s) Alert Acknowledgement…
-
Indicate whether the warning and alarm messages will be manually or automatically acknowledged
-
Click OK.
Configuring the Discovery Overrides
The solution automatically discovers the installation, binary, and library paths. This information can however be overridden.
To configure paths:
-
In the Console, right-click the server instance > KM commands > Configuration > Paths…
-
In the KM section, verify and possibly modify the Home, Temp, and Debug Directory Paths
-
In the Data Protector section, verify and possibly modify the Installation, the Data, and the Remote Temp Directory (remote nodes only) Paths
-
In the Binary Paths and Library Paths sections:
- From the list, select the paths to be removed
- In the Path field, enter the new path(s) to be included. If several paths are to be entered, separate them with a colon (:).
-
Click OK.
If you want to rediscover the paths, empty all fields, click OK, and restart the PATROL Agent.
Configuring Logs
By default, the following log files are monitored. These log file paths are relative to the HP Data Protector data directory (for example /var/opt/omni on UNIX/Linux and C:\ProgramData\OmniBack), unless the path is fully qualified.
| Log File | Description |
|---|---|
| On UNIX/Linux: | |
| log/debug.log | Debug Log |
| log/inet.log | Inet Log |
| log/media.log | Media Log |
| log/purge.log | IDB Purge Log |
| log/hpdp-idb-cp.log | IDB Connection Pooler Log |
| log/sm.log | Session Management Log |
| On Microsoft Windows: | |
| log\debug.log | Debug Log |
| log\inet.log | Inet Log |
| log\media.log | Media Log |
| log\purge.log | IDB Purge Log |
| log\hpdp-idb-cp.log | IDB Connection Pooler Log |
| log\server\omnisv.log | Data Protector Service Log |
| log\server\sm.log | Session Management Log |
Configuring the Log Filter
A log error filter can be configured to specify the regular expressions that will generate a warning or an alarm. Each time the KM finds these expressions in a log file (or in HPOLogText), the error message will be written to the HPOLogAlarmText or HPOLogWarningText parameter. By default, the default log filter is configured for the daily HP Data Protector messages file and the system log file. If you enabled additional log files for monitoring, you will have to customize the log filter by adding appropriate expressions for those log files.
| Error Expression | Set to Parameter | Status |
|---|---|---|
| Down | HPOLogAlarmText | Included |
For more information about the possible error messages, refer to the HP Data Protector System Administrator’s Guide and the HP Data Protector Troubleshooting Guide.
To configure the log error filter:
-
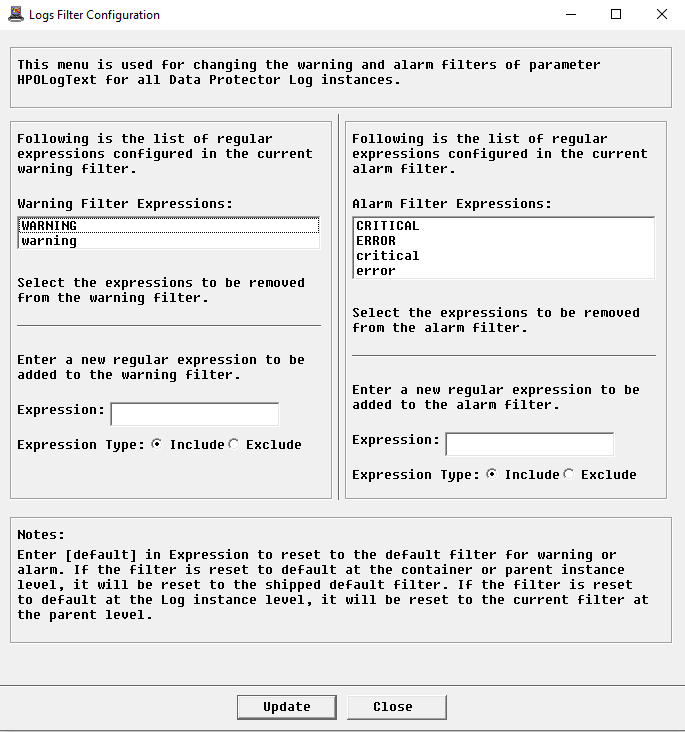
In the Console, right-click the Logs instance > KM Commands > Configuration > Logs Filter…
-
In the Warning Filter Expressions list, select the expressions that should be removed from the warning filter.
-
In the Alarm Filter Expressions list, select the expressions that should be removed from the alarm filter.
-
To add a new regular expression to the warning or alarm filter:
- In the Expression field, indicate the regular expression to be included (e.g.: skipping). Please note that regular expressions are case-sensitive.
- Select Include
-
To exclude a regular expression from the warning or alarm filter:
-
In the Expression field, indicate the regular expression to be excluded. You can also limit the exclusion to a particular expression already listed by using standard wildcard syntax.
-
Select Exclude
-
-
Click Update.
To revert to the default settings for either filter, type [default] as a new error expression for that filter, and click Update. If you revert to the default settings when accessed from the log instance level, the settings will revert to the parent or container instance level. To revert to the shipped default settings (as shown above), access this dialog from the log container instance. From this level you will also have the option to reset the configuration of any modified child instance.
Configuring the Log Scan Limit
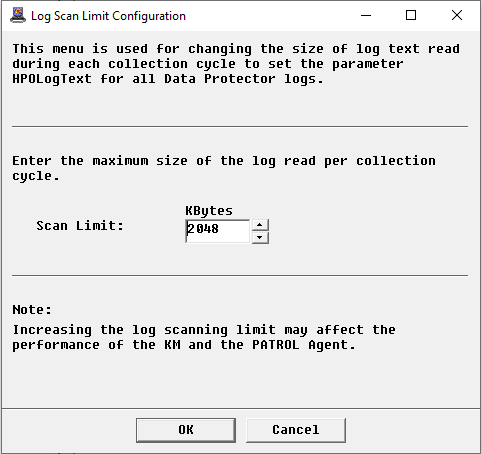
The HP Data Protector KM scans log files by reading the new log entries since the last data collection cycle. By default, only 500 Kbytes of data is scanned for each log file during each data collection cycle. This log scan limit can however be modified to better suit your requirements.
To customize the log scan limit:
-
In the Console, right-click the Log(s) instance > KM Commands > Configuration > Log(s) Scan Limit…
-
Indicate the amount of data that will be read by the KM during each data collection cycle.
-
Click OK.
Filtering Elements to Monitor
By default, the solution monitors all the discovered elements, except for Clients, Mount Requests, Standalone Devices and successful Sessions for which the monitoring can be manually enabled if required. To prevent excessive workload on agents and servers, and because the monitoring of some elements may be irrelevant for various reasons, you can also apply filters to indicate which elements will be monitored or not.
To filter elements to monitor:
-
In the Console, right-click one of the following instances depending on the elements that you wish to monitor:
- Clients > KM Commands > Configuration > Clients… to filter clients to be monitored.
- Daemons > KM Commands > Configuration > Daemons… to filter daemons to be monitored.
- Databases > KM Commands Configuration > Databases… to filter internal databases to be monitored.
- Logs > KM Commands > Configuration > Logs… to filter logs to be monitored.
- Specifications > KM Commands > Configuration > Specification… to filter specifications to be monitored. If a specification is disabled, the sessions related to that specification will not be monitored.
- Specifications > KM commands > Configuration > Specification Clients… to filter specification clients to be monitored.
- Libraries > KM Commands > Configuration > Libraries… to filter libraries to be monitored.
- Library Devices > KM Commands > Configuration > Library Devices… to filter library devices to be monitored.
- Standalone Devices > KM Commands > Configuration > Standalone Devices… to filter standalone devices to be monitored.
- Media Pools > KM Commands > Configuration > Media Pools… to filter media pools to be monitored.
Note: These menus are also available from the child instances and will apply to all objects created under the child instances.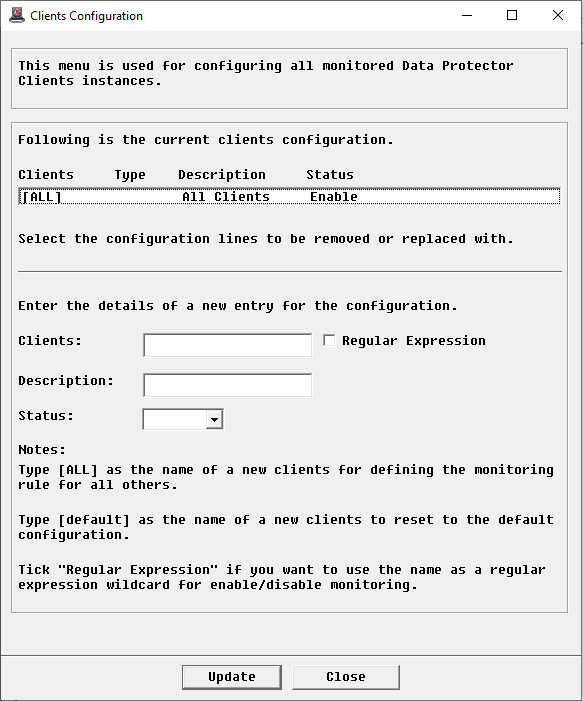
The
[ALL]entry ensures that all the elements found during PATROL discovery are instantiated and monitored. -
To enable elements for monitoring:
- In the current configuration list, select the elements to enable
- Select Enable
- Click Update
A log filter will have to be configured if you enable log files for monitoring.
-
To disable elements for monitoring:
- In the current configuration list, select the elements to disable
- Select Disable
- Click Update
All sessions associated to disabled specifications are not monitored.
Disabled instances will be instantiated in an OFFLINE state. Commands will not be executed, thus leaving parameters not set.
-
To delete elements for monitoring:
- In the current configuration list, select the elements to delete
- Select Delete
- Click Update
-
To add a new element to monitor:
- Type the name of the element to be monitored (as it appears in the PATROL console) or a regular expression to be monitored
- If needed, enter a description
- From the Status list, select Enable
- Click Update.
To revert to the default monitoring configuration, type [default] as a new entry and click Update.
-
Resume the procedure for all the application classes for which you wish to apply monitoring filters.
Configuring the Sessions Monitoring
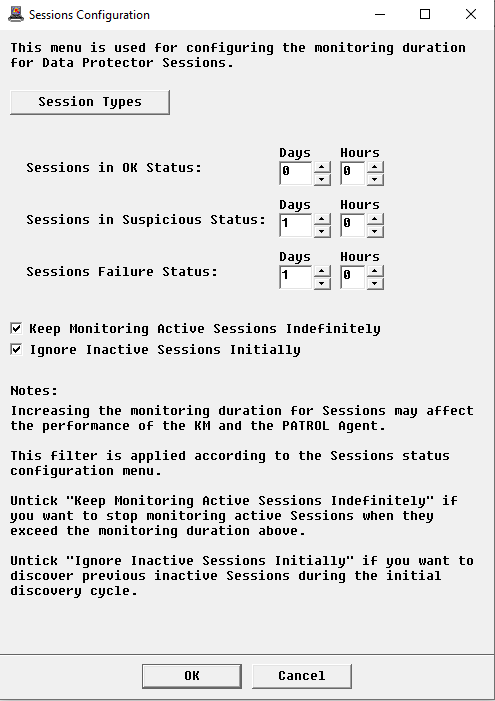
By default, HP Data Protector KM monitors failed and suspicious sessions for 1 day. The successfully completed sessions are not monitored. You can however modify these settings to better suit your requirements.
-
In the Console, right-click the Sessions instance > KM Commands > Configuration > Sessions…
-
Click Session Types to indicate the session types to be monitored in a comma-separated list. These types can be found in the omnirpt command manual. Click Accept. Leave this field blank to reset to the default configuration.
-
Indicate how long the sessions in OK, Suspicious, and Failure status will be monitored. If you:
- decrease the monitoring period, older sessions will be destroyed on the next data collection cycle
- increase the monitoring period, you will have to force a full data collection to ensure all sessions are instantiated. To force data collection, right-click the Sessions instance > KM Commands > Force Full Collection
-
Select:
- Keep Monitoring Active Sessions Indefinitely if you want to endlessly monitor active sessions
- Ignore Inactive Sessions initially if you want the inactive sessions not to be created in the initial discovery cycle. Initially discovering and monitoring inactive sessions may impact the performance of the application
-
Click OK.
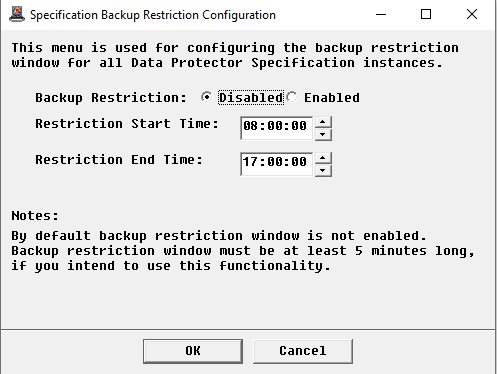
Configuring the Specification Backup Restriction Window
HP Data Protector KM can be configured to trigger an alert when a backup is started during a specific period of time:
-
In the Console, right-click:
- the Specifications instance > KM Commands > Configuration > Specifications Backup Restriction… to apply this customization to all specifications
- a Specification instance > KM Commands > Configuration > Specification Backup Restriction… to apply this customization to a specific specification
-
Select Enabled.
-
Indicate the Restriction Start and End Time. The restriction window should at least last 5 minutes.
-
Click OK.
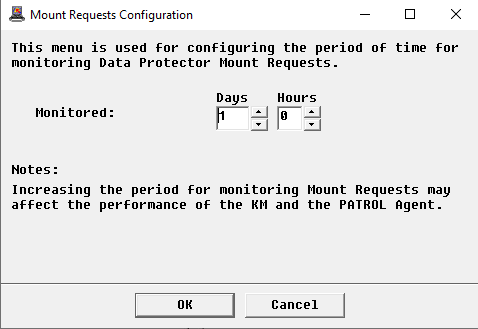
Configuring the Mount Requests Monitoring
By default, HP Data Protector KM monitors mount requests for 1 day. You can however modify these settings to better suit your requirements.
-
In the Console, right-click the Mount Requests instance > KM Commands > Configuration > Mount Requests…
-
Indicate how long the mount requests will be monitored. If you decrease the monitoring period, older mount requests will be destroyed on the next data collection cycle
-
Click OK.
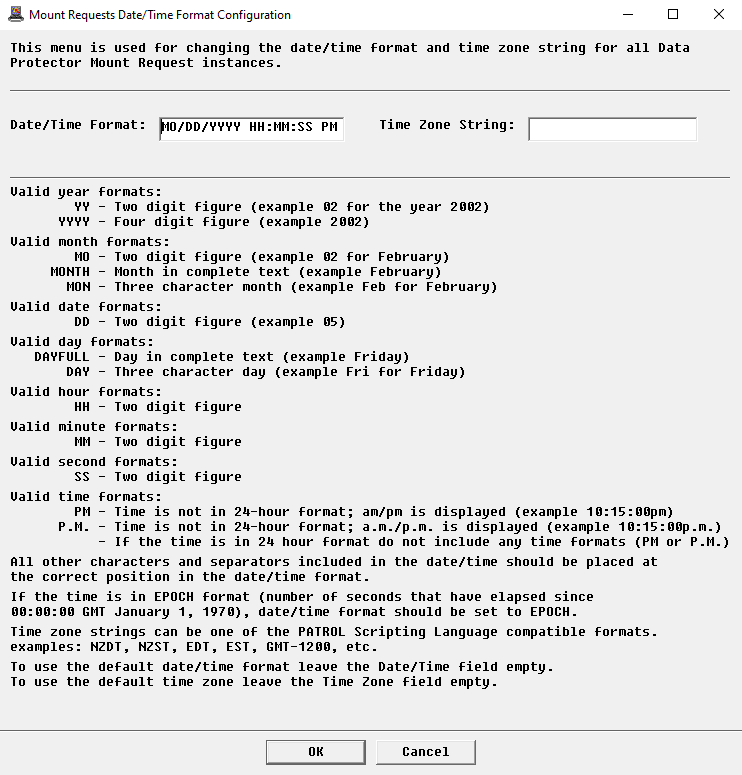
Configuring the Mount Requests Date/Time Format
The HP Data Protector KM uses HP Data Protector commands to determine the date and time of each mount request (used for calculating the elapsed time since the mount request was issued). Depending on your local system time zone and date/time format, the application may return a different date/time format.
To customize the mount request date/time format:
-
In the Console, right-click the Mount Requests instance > KM Commands > Configuration > Mount Requests Date/Time Format…
-
Indicate the expected Date/Time Format.
-
Indicate a PSL-compatible Time Zone String (e.g.: NZDT, NZST, EDT, EST, GMT-1200, etc.).
-
Click OK.
The new date/time format is then applied to all mount requests.
To revert to the default settings, blank out the Date/Time Format field and/or the Time Zone String field and click OK. The Time zone field used will be the local time zone on the managed node.
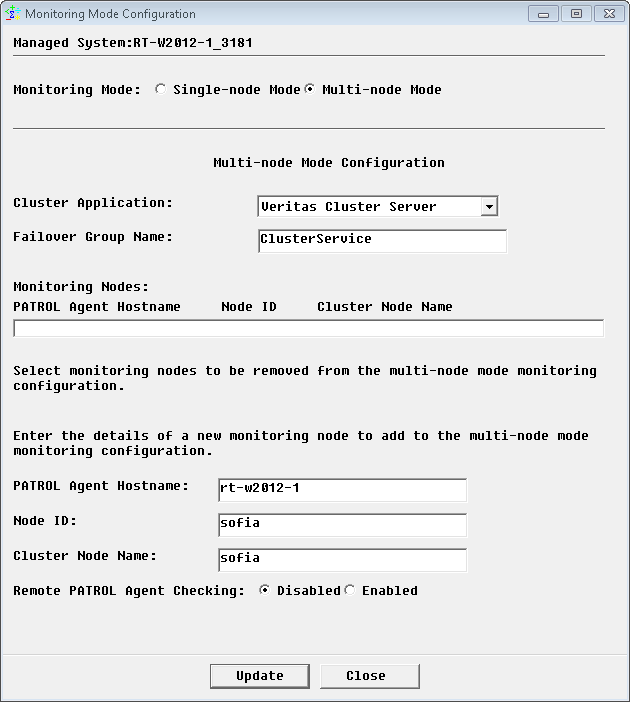
Configuring the Multi-Node Monitoring Mode
When HP Data Protector is installed in a cluster environment, i.e. active on one cluster node and passive on others, false alarms and duplicate alerts may occur. To avoid such situation, users need to configure HP Data Protector KM for PATROL in multi-node monitoring mode, if Data Protector is installed in a supported cluster.
To configure the multi-node monitoring mode:
-
In the Console, right-click the server instance > KM Commands > Configuration > Monitoring Mode…
-
Select Multi-node Mode.
-
From the Cluster Application pull-down list, select an appropriate cluster application.
-
In the Failover Group Name field, enter the failover group name, which is online on one cluster node and offline on the others. Leave this field blank if you previously selected Veritas Cluster File System. The HP Data Protector KM will then monitor the entire cluster from the active master system, which is identified by the
vxdctl -c modecommand. This method requiresvxconfigdin enable mode with its clustered state active. -
Provide the details of all managed nodes of the cluster to be configured in the multi-node mode:
- PATROL Agent Hostname: host where the PATROL Agent is installed
- Node ID: the unique ID of the Data Protector node as configured in the KM menu HP Data Protector instance > KM Command > Configuration > Data Protector Nodes
- Cluster Node Name: the hostname defined in the selected Cluster Application.
-
Click Update.
-
Resume the procedure for all the other Data Protector nodes and click Update.
-
Check the Remote PATROL Agent Checking option if there are more than one PATROL Agent involved in the multi-node mode configuration above. If enabled, the KM queries the other PATROL Agents to check the monitoring status of other nodes.
-
Click Close.
-
If the Remote PATROL Agent Checking is Enabled, you will have to provide all the information required to communicate with the PATROL Agents (protocol, port number, credentials, attempts and timeout).
-
Click Close.
The Data Protector server will then be monitored through the master or online node in Active Multi-node Mode. The other nodes, which are standing by for a failover, will be in Passive Multi-node Mode, monitoring only the components that are not visible from the active node.
If a managed node is unable to check the monitoring status of the active managed node, it will change to Temporary Single-node Mode allowing full monitoring. It will remain in Temporary Single-node Mode until it finds the active node in full monitoring mode again.
If the Remote PATROL Agent Checking is Disabled, while there are more than one PATROL Agent involved, the managed node on the master or online node will be in Active Multi-node Mode and all others will be in Passive Multi-node Mode, without checking the monitoring status of the active node. In addition, the above procedure to configure Multi-node Mode (server instance > KM Commands > Configuration > Monitoring Mode) needs to be repeated from each PATROL Agent involved.
Configuring the Node Status
HP Data Protector KM allows you to manually customize the regular expressions used for the node status:
-
In the Console, right-click the Server instance > KM Commands > Configuration > Node Status…
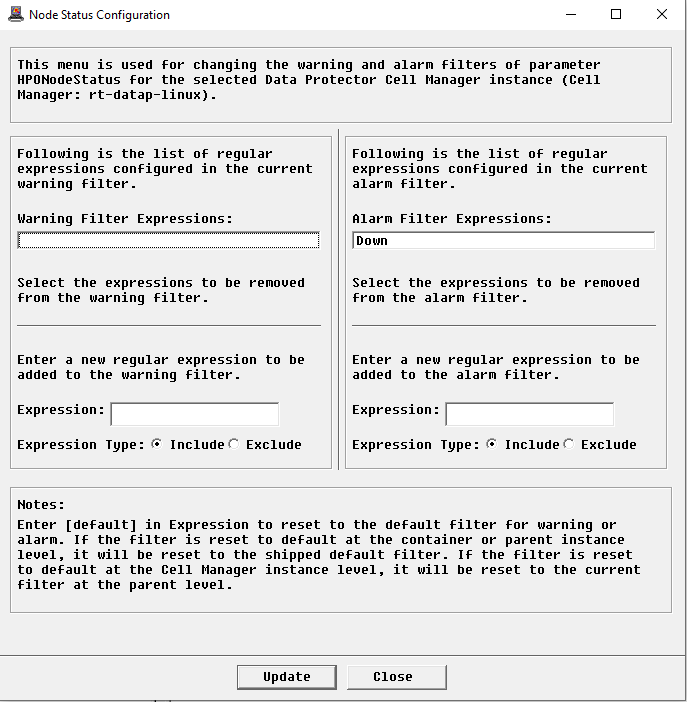
-
Provide the Node Status Alarms and Warnings: Enter the regular expressions to determine the Node Status in Alarm or Warning status. This regular expression will be used on the result from Data Protector command: “omnisv -status” on the Data Protector server
By default, the following “Included” expressions are checked. If detected, they set the parameter HPONodeStatus to alert, unless the message also contains an “Excluded” expression. Type [default] to reset to the default configuration.
| Error Expression | HPONodeStatus | |
|---|---|---|
| Down |
|
Failure |
- Click Update.