-
Home
- TrueSight
Configure CMA Policies
This section explains the settings required to configure HP Data Protector KM via a TrueSight/Helix CMA policy.
Configuring After Installation
Once HP Data Protector KM is installed, you will have to configure the HP Data Protector KM Monitor Types through policies. Policies enable you to deploy configurations on PATROL Agents and monitoring solutions, such as HP Data Protector KM in an automated way. Policies are designed to define and configure monitoring criteria and apply them to the specified PATROL Agents. The configuration criteria are automatically pushed to the PATROL Agents on which the policy is applied. When a monitoring policy is applied to a PATROL Agent, the device is automatically added to the list of monitored devices.
To create a monitoring policy:
-
Log on to the TrueSight console.
-
In the navigation pane, expand Configuration and select Infrastructure Policies.
-
In the Infrastructure Policies page, ensure that the Monitoring tab is selected and click Create Policy.
-
In the Create Monitoring Policy page, specify the monitoring policy properties:
Step 1 - Define the General Properties
Property Description Name Name for the policy. The policy names must be unique. In an environment with tenants, the policy names must be unique for a single tenant. It is a mandatory field. Description (Optional) A brief description about the policy. Associated User Group Name of the user group that is associated with the PATROL Agents as defined in the Authorization Profile or in the PATROL Agent ACLs. The policy is applicable to these PATROL Agents. Share with User Group Specify whether this policy is to be shared with the users across the associated user group or not. This property can be viewed in READ-ONLY mode by other users of the associated user group. Only the owner of the policy can modify this property. Precedence Priority of the policy. Based on the precedence number that you configure, the configuration is applied to the PATROL Agents and the Infrastructure Management servers. The precedence number ranges from 0 to 999. A lower number indicates a higher precedence. The default value is 900. The configuration from a policy with a higher precedence overrides the configuration from a policy with a lower precedence. If two policies have the same precedence number, then the configuration from the latest created policy takes priority. Enable Policy Indicates whether the policy is enabled or disabled. By default, the policy is disabled. If you do not enable a policy when you create it, the policy configurations are not applied to the PATROL Agents and the Infrastructure Management Servers. If you disable any existing policy, the policy configurations are removed from the PATROL Agents and the Infrastructure Management servers, where the policy was applied. Step 2 - Select the PATROL Agents
Define conditions to select the PATROL Agents on which you want to apply the policy:
- Select a property.
- Select an operator to create the condition. The available operators depend on the property that you select.
- Specify a value for the selected property.
- (Optional) To add more than one condition, click the

- (Optional) To group the conditions, use the parentheses and Boolean operators from their corresponding lists.
The Add Monitor Types dialog box presents configuration fields for compatible BMC PATROL monitoring solutions that are located in the Central Monitoring Repository.
Step 3 - Select the Required Monitor Type
-
Click the Monitoring tab.
-
Click Add Monitoring Configuration.
-
In the Add Monitoring Configuration dialog box, configure the properties:
- From the Monitoring Solution menu, select HP Data Protector KM.
- From the Version menu, select the required version.
The Monitor Profile HP Data Protector KM is automatically selected.
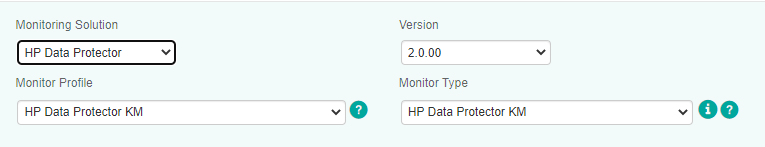
Refer to the table below to know which monitor types are available and their function:
Monitor Type Description HP Data Protector KM (REQUIRED) To set the general settings of the HP Data Protector monitoring solution (credentials, debug mode, instances, multi-node mode, etc.). Once this monitor type is configured, all other monitor types are automatically monitored. Their default behavior can however be modified by selecting them from the Monitor Type list. No other monitor types can be configured as long as HP Data Protector KM is not configured. Data Protector Client To modify the client default monitoring. Data Protector Daemon To modify the daemon default monitoring. Data Protector Library To modify the library default monitoring. Data Protector Library Device To modify the library device default monitoring. Data Protector Log To modify the log default monitoring. Data Protector Media Pool To modify the media pool default monitoring. Data Protector Mount Request To modify the mount request default monitoring. Data Protector Session To modify the session default monitoring. Data Protector Specification To modify the specification default monitoring. Data Protector Specification Client To modify the specification client default monitoring. Data Protector Standalone Device To modify the standalone device default monitoring. Step 4 - Configure the Selected Monitor Type
- Depending on the selected Monitor Type, the available fields will vary. Refer to appropriate section below to know how to configure them.
- Click Save to apply your changes to the selected PATROL Agent(s).
Step 5 - Update the Status Mappings
The predefined status mappings can be changed, using the Monitoring Studio Web Interface.
To edit a monitoring policy
- Log on to the TrueSight console.
- In the navigation pane, expand Configuration and select Infrastructure Policies.
- In the Infrastructure Policies page, locate the monitoring policy you wish to modify, click its action button

- In the Edit Monitoring Policy page, locate the monitoring configuration you wish to modify and click its action button

- Customize the configuration.
- Click Save to apply your changes to the selected PATROL Agent(s).
Configuring Data Protector Servers Settings
Before using HP Data Protector KM, you need to configure the monitoring settings for the HP Data Protector KM Monitor Type. You will then be able to create and customize other Monitor Types according to the component(s) you wish to monitor.
To specify the options that will constitute the Data Protector monitoring settings:
-
In the Add Monitoring Configuration dialog box, configure the properties:
- From the Monitoring Solution menu, select HP Data Protector KM
- From the Version menu, select the required version
The Monitor Profile HP Data Protector KM is automatically selected.
-
In the Data Protector Monitoring Settings section, click Add.
-
Specify the settings for the Data Protector Host to be monitored:
- In the Hostname/IP Address/FQDN field:
- for a local host, enter localhost to apply these settings to all PATROL Agents installed on the Data Protector Servers
- for a remote host, enter the hostname or IP address of the remote Data Protector Host to monitor it remotely from the PATROL Agent
- In the System Type field, specify whether the Data Protector system is a UNIX/Linux or Windows system.
- (Optional - Remote Monitoring Only) Click the Create a Device in the Console box if you want the Data Protector server to appear as a separate device in TrueSight.
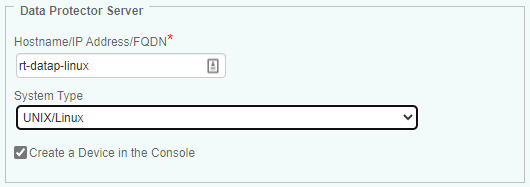
- In the Hostname/IP Address/FQDN field:
-
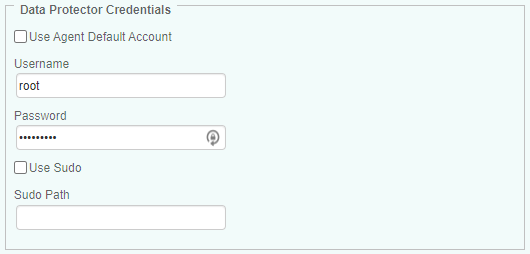
Set the Data Protector Credentials:
- To use the default PATROL Agent Account, check the Use Agent Default Account option
- To use a different user account, enter the login details in the Username and Password fields
- (UNIX/Linux Only) If the user account has sudo privileges, check the Use Sudo box and indicate the sudo binary file path, if installed in a non-default path.
-
(Optional) Define the Advanced Settings:
-
Click OK twice.
-
Click Save.
Configuring Advanced Settings
Once the HP Data Protector server to be monitored and the account to be used are specified, you can configure the following advanced settings:
- The debug mode
- The remote connection settings
- The maximum number of instances
- The multi-node monitoring mode
- The Data Protector server discovery overrides
Enabling the Debug
The KM Debug Mode should not be enabled, unless for troubleshooting. You can follow these steps to enable/disable KM debug.
Configuring the Remote Connection Settings
To configure the remote connection settings:
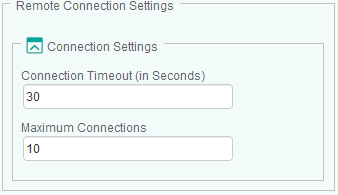
- In the Connection Timeout (in Seconds) field, enter the number of seconds after which the connection to the remote node will time out
- In the Maximum Connections field, enter the maximum number of simultaneous connections allowed to the remote node
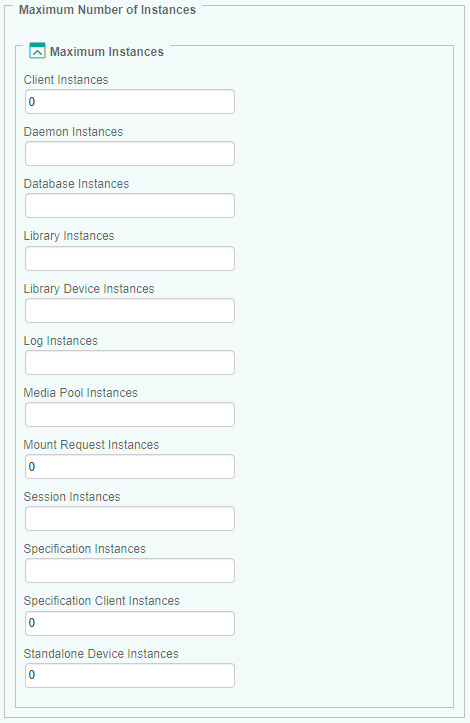
Configuring the Maximum Number of Instances
The solution discovers and monitors all the instances, except for Clients, Specification Clients, Mount Requests and Standalone Devices that are disabled by default. Because there may be a very large number of instances to monitor that may represent an important workload to the agents and the TrueSight servers, it is recommended to only monitor the critical ones. This can be done by configuring the instance limits.
To configure the maximum number of instances:
-
Click the action button

-
In the Data Protector Monitoring Settings panel, scroll down to the Maximum Number of Instances section.
-
For each monitored element, indicate the maximum number of instances to be displayed, or enter 0 (zero) in the relevant field to disable the monitoring of a specific element. (By default, the maximum number of instances is left empty to allow an unlimited number of instances).
-
Click OK twice.
-
Click Save.
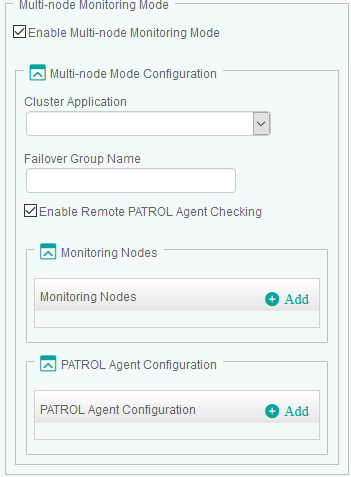
Configuring the Multi-Node Monitoring Mode
When an application is installed in a cluster environment, i.e. active on one cluster node and passive on others, false alarms and duplicate alerts may occur. To avoid such situation, users need to configure HP Data Protector KM in multi-node monitoring mode, if Data Protector is installed in a supported cluster.
To configure the multi-node monitoring mode:
-
Click the action button

-
In the Data Protector Monitoring Settings panel, scroll down to the Multi-node Monitoring Mode section.
-
Check the Enable Multi-node Monitoring Mode option.
-
Configure the Multi-node Mode:
- Select the appropriate Cluster Application
- Indicate the Failover Group Name. Leave this field blank if you have previously selected Veritas Cluster File System. The HP Data Protector KM will then monitor the Data Protector system from the active master system, which is identified by
vxdctl -c modecommand. This method requiresvxconfigdin enable mode with its clustered state active.
-
(Optional) Check the Enable Remote PATROL Agent Checking option to allow the solution to check the monitoring mode of the remote PATROL Agents. If the Remote PATROL Agent Checking is disabled, the solution will monitor actively through active cluster node or on the node where failover group is online and will not check the monitoring status of the HP Data Protector KM on the other PATROL Agent nodes.
-
In the Monitoring Nodes section:
-
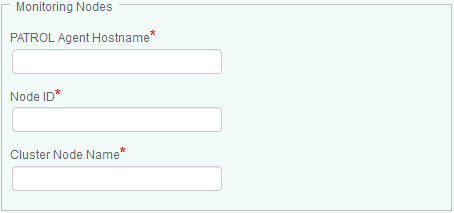
Click Add to configure the details of all managed nodes of the cluster to be configured in the multi-node mode
-
Provide the PATROL Agent Hostname (host where the PATROL Agent is installed), the Node ID (the unique ID of the Data Protector node derived from the hostname in the Data Protector Server configuration), and Cluster Node Name (the hostname defined in the selected Cluster Application)
-
Click OK
-
Repeat the procedure for each Data Protector node that is part of the multi-node mode configuration
-
-
If the Enable Remote PATROL Agent Checking option is selected, click Add in the Remote Agent Configuration section, to provide all the information required to communicate with the PATROL Agents. There should be one entry per each PATROL Agent.
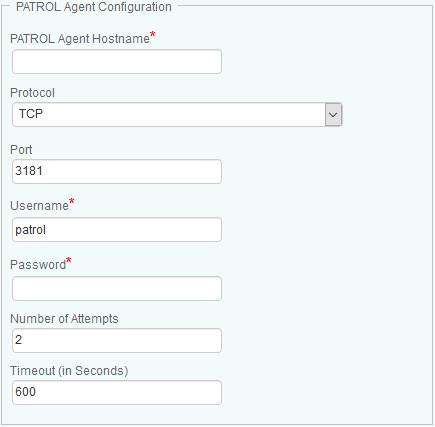
- Provide the PATROL Agent Hostname
- Select the Protocol you wish to use to connect to the PATROL Agent
- Enter the Port number you wish to use to connect to the PATROL Agent
- Provide the Username and Password you wish to use to connect to the PATROL Agent
- In the Number of Attempts field, specify the number of times the solution will try to communicate with the remote PATROL Agent before failing over
- Enter the timeout you wish to set, in seconds, between each attempt
-
Click OK twice.
-
Click Save.
The Data Protector server will then be monitored through the master or online node in Active Multi-node Mode. The other nodes, which are standing by for a failover, will be in Passive Multi-node Mode, monitoring only the components that are not visible from the active node.
If a managed node is unable to check the monitoring status of the active managed node, it will change to Temporary Single-node Mode allowing a full Data Protector monitoring. It will remain in Temporary Single-node Mode until it finds the active node in full monitoring mode again.
If the Remote PATROL Agent Checking is Disabled, while there are more than one PATROL Agent involved, the managed node on the master or online node will be in Active Multi-node Mode and all others will be in Passive Multi-node Mode, without checking the monitoring status of the active node. In addition, the above procedure to configure Multi-node Mode needs to be repeated from each PATROL Agent involved.
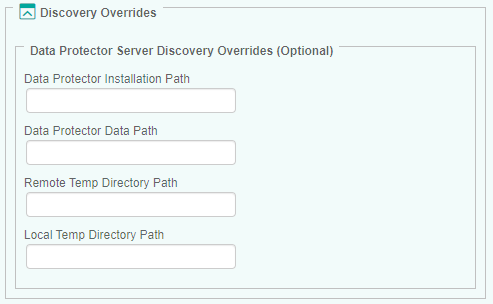
Configuring the Data Protector Server Discovery Overrides (Optional)
The solution automatically discovers the Data Protector installation, the temporary directory paths used by the HP Data Protector KM, and the node status. This information can however be overridden.
To configure Data Protector server discovery overrides:
-
Click the action button

-
In the Data Protector Monitoring Settings panel, scroll down to the Discovery Overrides section.
-
Specify the Data Protector Server Discovery Overrides options:
- Data Protector Installation Path: Provide the path to the directory where the Data Protector software is installed. By default, HP Data Protector KM automatically locates the Data Protector software installation directory if you have installed the solution with the default recommended settings. If you have chosen to install the solution in a custom directory, you are required to provide its location.
- Data Protector Data Path: Provide the path to the directory where the Data Protector data is stored.
- Remote Temp Directory Path: Provide the path to the directory where the temporary files are saved on remote nodes. Default is
/var/tmp(on UNIX/Linux) orC:\Windows\Temp(on Windows). - Local Temp Directory Path: Provide the path to the directory where the temporary files are saved on the PATROL Agent node (Default is
<PATROL_HOME>/lib/HPO/tmpwhere<PATROL_HOME>is the PATROL Agent installation path)
-
Click OK twice.
-
Click Save.
Configuring Other Monitor Types
By default, the solution monitors all the discovered elements, except for Clients, Mount Requests, Standalone Devices and successful Sessions for which the monitoring can be manually enabled if required. To prevent excessive workload on agents and TrueSight servers, and because the monitoring of some elements may be irrelevant for various reasons, you can also apply filters to indicate which elements will be monitored or not.
Filtering options are available for the following monitor types: Data Protector Client, Data Protector Daemon, Data Protector Library, Data Protector Library Device, Data Protector Media Pool, Data Protector Specification, Data Protector Specification Client, and Data Protector Standalone Device.
To configure elements to be monitored:
-
Select the Monitor Type for which you wish to apply filters.
-
In the Monitor panel, click Add.
-
In the Hostname field, enter:
- localhost to apply these settings to all PATROL Agents installed on Data Protector Servers
- a hostname or IP address to apply these settings to a specific server.
-
Configure the Filtering options:
- In the Keep Only… section, click Add and identify the element you wish to monitor. Enter the name of the element or identify it by using a regular expression (example:
prod-client*). Click OK to validate. Repeat the operation for any other element you wish to include in the monitoring process. - In the Exclude… section, click Add and identify the element you do not want to monitor. Enter the name of the element or identify it by using a regular expression (example:
test-client*). Click OK to validate. Repeat the operation for any other element you wish to exclude from the monitoring process.
- In the Keep Only… section, click Add and identify the element you wish to monitor. Enter the name of the element or identify it by using a regular expression (example:
-
The Additional <Elements>(manual discovery) section allows you to add elements manually, when they are not automatically discovered:
- Click Add and enter the name of the element you wish to add to the monitoring environment. Click OK to validate. Repeat the operation for each element you want to monitor.
- (Optional) Enter a short description that will allow you to quickly identify the added element.
-
Click OK to validate.
Configuring Data Protector Sessions
By default, HP Data Protector KM monitors the sessions that are in suspicious or failure status for 24 hours. Successfully completed sessions are not monitored. This monitoring duration can however be modified to better suit your requirements.
To configure Data Protector sessions:
-
From the Add Monitoring Configuration panel, select Data Protector Session from the Monitor Type list.
-
In the Data Protector Session panel, click Add.
-
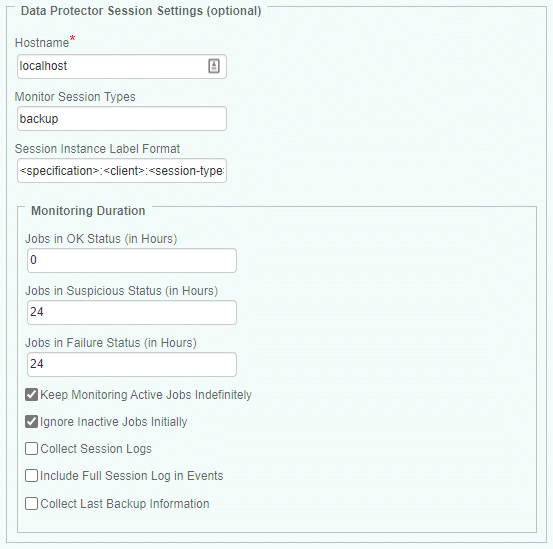
In the Hostname field, enter:
- localhost to apply these settings to all PATROL Agents installed on Data Protector servers
- a hostname or IP address to apply these settings to a specific server
-
In the Monitor Session Types field, indicate the session types to be monitored in a comma-separated list. These can be found in the omnirpt command manual. Leave this field blank to use the default configuration or type [ALL] to monitor all session types.
-
In the Session Instance Label Format field, enter the session instance label format to be used in the console. The keywords <specification>, <client>, <session-id>, <session-type> and <start-time> are supported. Using <start-time> will create a large number of dynamic instances in the BMC TrueSight/Helix console. Leave this field blank to use the default configuration.
-
In the Monitoring Duration section:
- Indicate how many hours the sessions in OK, Suspicious, and Failure status will be monitored
- Select Keep Monitoring Active Sessions Indefinitely if you prefer to endlessly monitor active sessions
- Select Ignore Inactive Sessions Initially if you prefer to monitor only the active sessions during initial collection cycle
- Select Collect Session Logs if you prefer to collect the session logs in the HPOSessionText parameter
- Select Include Full Session Log in Events if you prefer to include the full session log in the session events instead of only the last message
- Select Collect Last Backup Information if you prefer to collect the last backup information under Specification and Specification Client instances.
-
Click OK to validate.
Configuring Logs
By default, HP Data Protector KM monitors the logs found under the Data Protector Data Path. Additional logs can be added in the TrueSight/Helix CMA policy. A log filter is configured by default for these log files to ensure warnings or alarms are triggered when a specific error message is found. These regular expressions can be modified using the Monitoring Studio Web Interface.
Configuring the Log Scan Limit
HP Data Protector KM scans log files by reading the new log entries since the last data collection cycle. By default, only 500 KBytes of data is scanned for each log file during each data collection cycle. This log scan limit can however be modified to better suit your requirements.
To customize the log scan limit:
-
From the Add Monitoring Configuration panel, select Data Protector Log from the Monitor Type list.
-
In the Data Protector Log Settings panel, click Add.
-
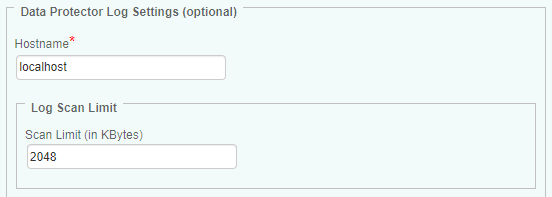
In the Hostname field, enter:
- localhost to apply these settings to all PATROL Agents installed on the Data Protector server
- a hostname or IP address to apply these settings to a specific server
-
Indicate the amount of data (in KBytes) that will be read by the monitoring solution during each data collection cycle.
-
Click OK twice.
-
Click Save.
Configuring Custom Data Protector Logs Monitoring
To override the default configuration and add additional log files, you will have to configure the custom Data Protector Logs monitoring as follows:
-
From the Add Monitoring Configuration panel, select Data Protector Log from the Monitor Type list.
-
In the Data Protector Log Settings panel, click Add.
-
In the Custom Data Protector Logs section, click Add.
-
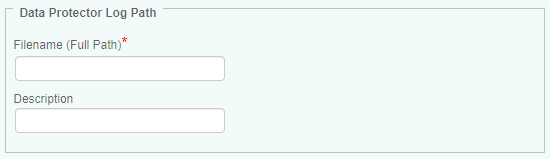
In the Filename (Full Path) field, enter the full path to the Data Protector Log file to be monitored using backslash (/) as the file path separator (example:
\var\adm\messages). -
(Optional) Enter a brief description of the Data Protector log.
-
Click OK.
-
Click OK twice.
-
Click Save.
The KM is preconfigured with regular expressions that will generate a warning or an alarm when found in the custom Data Protector log. These regular expressions can be changed through the Monitoring Studio Web Interface.
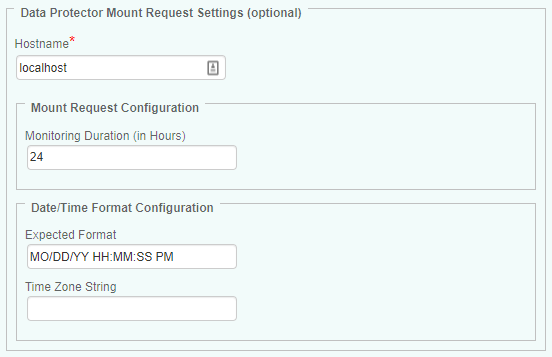
Configuring Data Protector Mount Requests
By default, HP Data Protector KM monitors all mount requests for 24 hours, if enabled. This monitoring duration can however be modified to better suit your requirements.
To configure Data Protector mount requests:
-
From the Add Monitoring Configuration panel, select Data Protector Mount Request from the Monitor Type list.
-
In the Data Protector Mount Request panel, click Add.
-
In the Hostname field, enter:
- localhost to apply these settings to all PATROL Agents installed on Data Protector Master and Media servers
- a hostname or IP address to apply these settings to a specific server
-
In the Mount Request Configuration section, indicate how many hours the mount requests will be monitored
-
If the date/time format returned by Data Protector commands is different from your local system time zone, you will have to configure it in the Date/Time Format Configuration section:
- Indicate the Expected Format. Refer to the table below to know the valid formats:
Format Description Default Date/Time Format Leave blank. EPOCH Set EPOCH, if the time format is the number of seconds that have elapsed since 00:00:00 GMT January 1, 1970 Year Formats YY Two digit figure Example: 12 for the year 2012 YYYY Four digit figure Example: 2012 Month Formats MO Two digit figure Example: 02 for February MONTH Month full name Example: February MON Three character name Example: Feb Date Formats DD Two digit figure Example: 05 Day Formats DAYFULL Day full name Example: Friday DAY Three character name Example: Fr Hour Formats HH Two digit figure Minute Formats MM Two digit figure Second Formats SS Two digit figure Time Formats [blank] Time is in 24-hour format PM Time is in 12-hour format; am/pm is displayed Example: 10:15:00pm P.M Time is in 12-hour format; a.m/p.m is displayed Example: 10:15:00p.m - Indicate a PSL-compatible Time Zone String (e.g.: NZDT, NZST, EDT, EST, GMT-1200, etc.)
-
Click OK to validate.
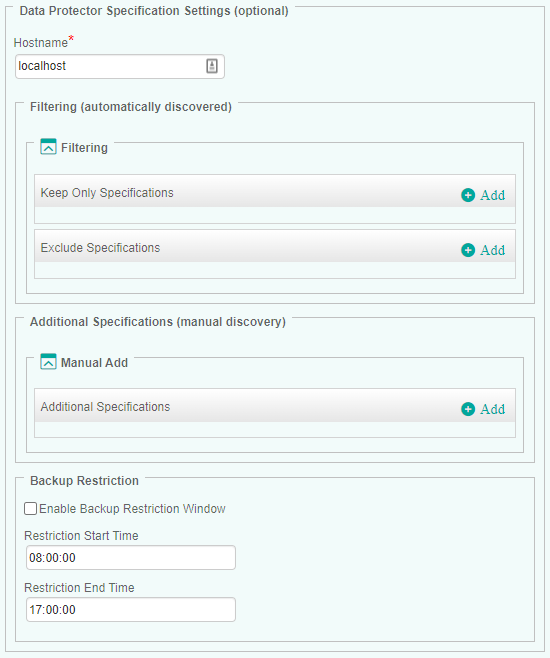
Configuring Data Protector Specifications
By default, HP Data Protector KM monitors all specifications configured on the master server. Filters can however be applied to better suit your requirements. Additionally, a restriction window can be configured for specifications backups.
To configure Data Protector specifications:
-
From the Add Monitoring Configuration panel, select Data Protector Specification from the Monitor Type list.
-
In the Data Protector Specification panel, click Add.
-
In the Hostname field, enter:
- localhost to apply these settings to all PATROL Agents installed on Data Protector Servers
- a hostname or IP address to apply these settings to a specific server.
-
Configure the Filtering options:
- In the Keep Only Specifications section, click Add and identify the Data Protector specification you wish to monitor. Enter the name of the Data Protector specification or identify it by using a regular expression (example:
prod-*). Click OK to validate. Repeat the operation for any other Data Protector specification you wish to include in the monitoring process. - In the Exclude Policies section, click Add and identify the Data Protector specification you do not want to monitor. Enter the name of the Data Protector specification or identify it by using a regular expression (example:
test-*). Click OK to validate. Repeat the operation for any other Data Protector specification you wish to exclude from the monitoring process.
- In the Keep Only Specifications section, click Add and identify the Data Protector specification you wish to monitor. Enter the name of the Data Protector specification or identify it by using a regular expression (example:
-
The Additional Policies (manual discovery) allows you to add Data Protector policies manually, when they are not automatically discovered:
- Click Add and enter the name of the Data Protector specification you wish to add to the monitoring environment. Click OK to validate. Repeat the operation for each Data Protector specification you want to monitor.
- (Optional) Enter a short description that will allow you to quickly identify the added Data Protector specification.
-
If you want a warning to be triggered when a backup is started during a specific period of time, configure a Backup Restriction Window:
- Check the Enable Backup Restriction Window option
- Indicate the Restriction Start and End Time. The format required is HH:MM:SS and the restriction window must at least last 5 minutes.
-
Click OK to validate.